3.1 Overview of cybersecurity technical development
Application of the avoidance sector threshold to the actual avoidance action is as follows: one of the detailed tasks of the Korean MASS project, cybersecurity technology development, is to develop systems and related technology standards that utilize the latest cybersecurity technologies to detect, defend, and respond to cyber threats inside and outside autonomous ships.
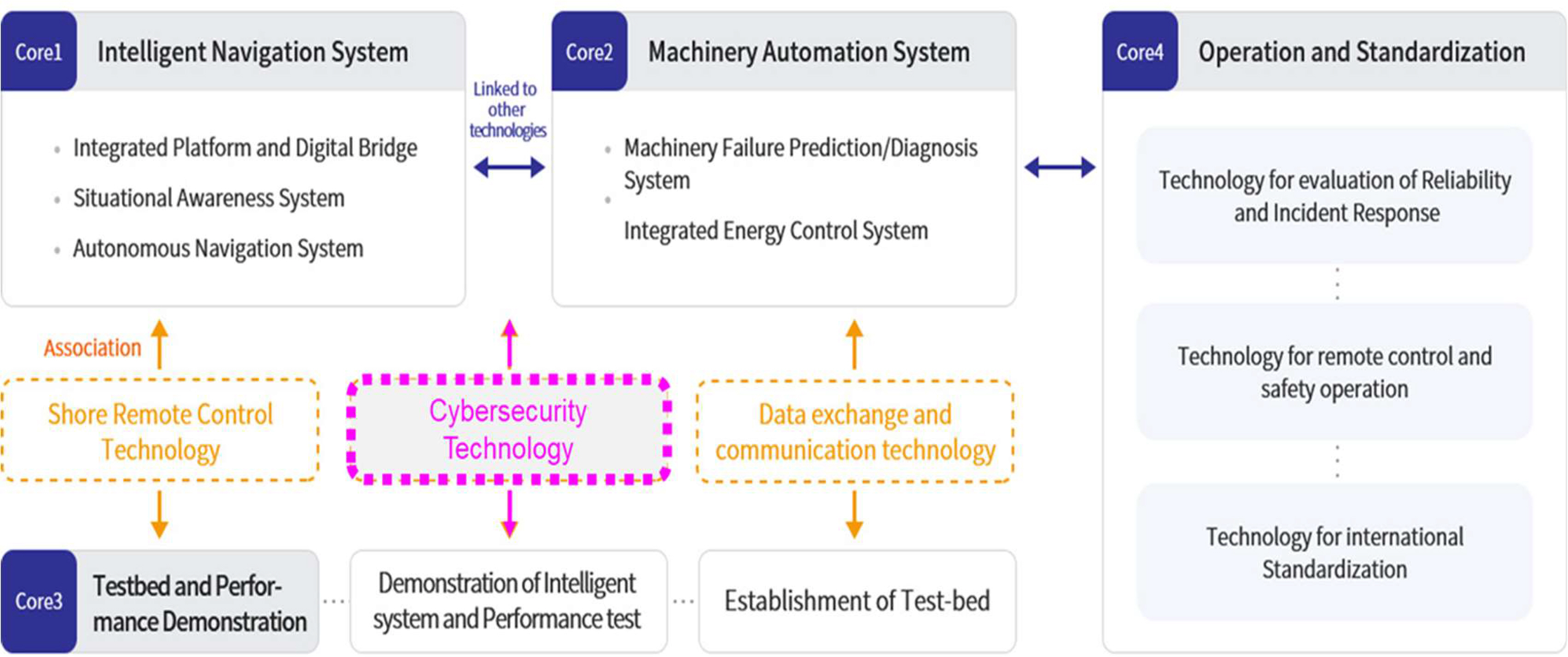
Fig. 3 shows the overall configuration of the cybersecurity technology development for MASS, which consists of four steps: 1) cybersecurity gateway development, 2) integrated cybersecurity management system development, 3) cybersecurity technology standard development, and 4) cybersecurity system operation test and test scenario development.
First, the cybersecurity gateway which is a critical aspect of the MASS is developed. It is an AI-based ship network security device(AI-SNSD) that includes various features such as authentication and encryption technology for ship-to-external communication, detection and blocking of attacks based on a deep packet inspection(DPI) analysis of external incoming traffic.
The second aspect of the MASS's cybersecurity development is the development of an integrated cybersecurity management system. This system will include various features, such as data processing technology, cybersecurity data collection and analysis technology, dashboard development, in-ship ICT asset management, and public-information-based cyber asset vulnerability analysis technology.
Third, the development of cybersecurity technology standards includes the development of guidelines for the cybersecurity-type approval of autonomous ships, the development of cybersecurity gateway technology standards for autonomous ships, and the development of guidelines for test procedures for autonomous ship cybersecurity systems.
Fourth, the development of actual cybersecurity system operation tests and test scenarios includes the collection and analysis of current cybersecurity status data of existing ships, the development of cybersecurity test plan scenarios based on the analyzed data, the application of autonomous ships, and testing and verification.
This study focuses on the ŌĆśDevelopment of cybersecurity gateway products for MASSŌĆÖ as a key component of the cybersecurity technology development tasks.
3.2 Configuration of AI-based ship network security device(AI-SNSD)
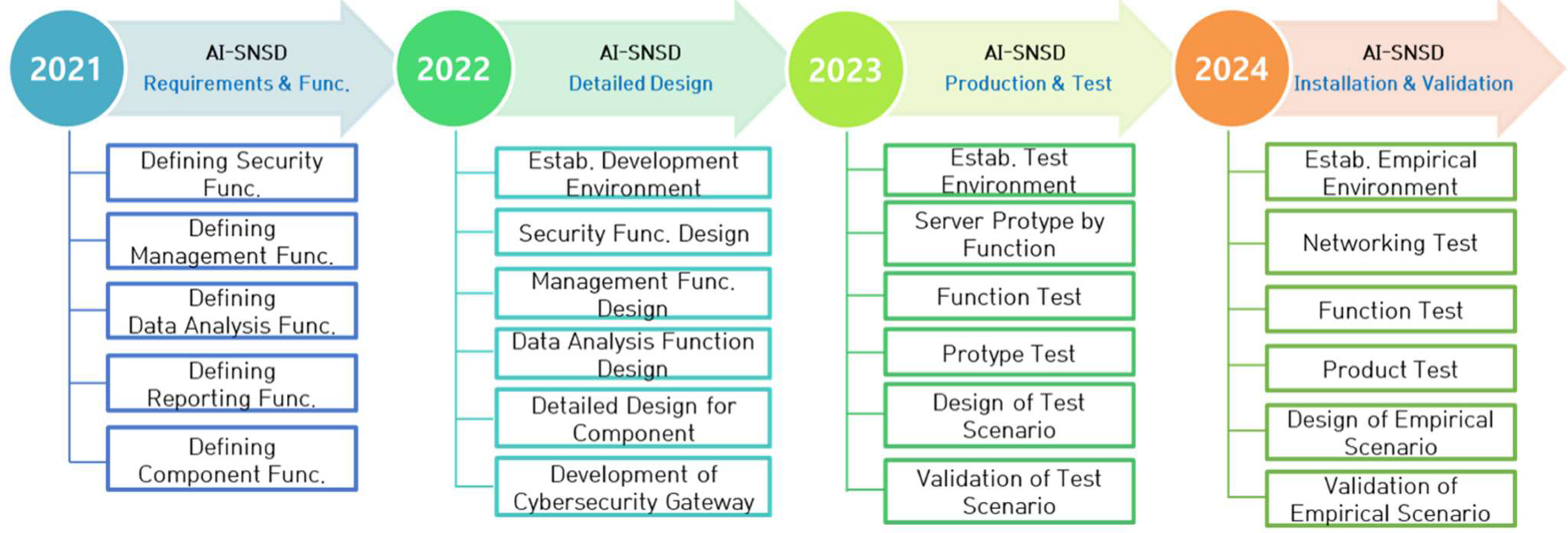
Functional requirements for MASS operations were identified in 2021 to develop a security gateway for MASS ships. In the case of AI-SNSD, functions such as firewall, intrusion detection and protection(IDPS), anomaly detection, and deep packet inspection are required. In the case of Data-Archiving, functions such as collection of data(packet), analysis of network status, decompression and re-compression of collection data(packets) files, failover of collection data(packet) forwarding, prevention of disk overflow, and data transmission are required. In the case of Data-Gathering, functions such as data(packet) collection, filtering, forwarding, file compression, forwarding failover, and collection interruption are required. In the case of Management-System, functions such as policy management, certificate management, certificate issuance, log management, monitoring, and notice are required. In the case of Certificate-Management-System, functions such as self-protection, authentication, and encrypted communication are required.
Based on the identified functional requirements, the ship consisted of six components(C1: AI-SNSD, C2: Data Archiving, C3: Data Gathering, C4: Network Device, C5: Digital Bridge, and C7: Integrated Security Management System), and the shore consisted of three components(C6: Certificate Management Server, C8: Machine Learning Server, C9: Data Storage Server).
C1's SDA and SDB transmit data stored from data-gathering and network devices to AI-SNSD. SDC and SDI allow AI-SNSD to receive upper/lower certificates through a certificate management server and transmit policies and data defined by AI-SNSD to an integrated security management system on land. SDM and SDS receive the results of AI-SNSD learning based on data from the machine learning server and transmit the data to be learned from the machine learning server to the data storage server. The DA of C2 stores the data collected from the data-gathering device present in each zone, and the NA stores the data collected from the network device. In addition, SDA transmits data stored in data-gathering and network devices to AI-SNSD. The DA and ND of C3 transmit data stored by the data-gathering device installed in each zone to the data-archiving device. ND and NA of C4 transmit the generated data to the data-gathering device. The SDB of C5 receives associated data from AI-SNSD. The SDC of C6 serves as a certificate management server for issuing AI-SNSD certificates. The SDI of C7 receives data such as those of policies defined by AI-SNSD and provide necessary data for management/operation to AI-SNSD through the integrated security management system. The SDM of C8 transmits the results learned from the machine learning server to the AI-SNSD, and the MS receives data from the data storage server to be learned by the machine learning server. The SDS of C9 receives and stores data to be used for learning from the machine learning server from AI-SNSD, and MS transmits the data stored in the storage server to the machine learning server.
The interface connections for each component are shown in
Fig. 4. The interface definitions and function descriptions for each component are listed in
Tables 1 and
2.
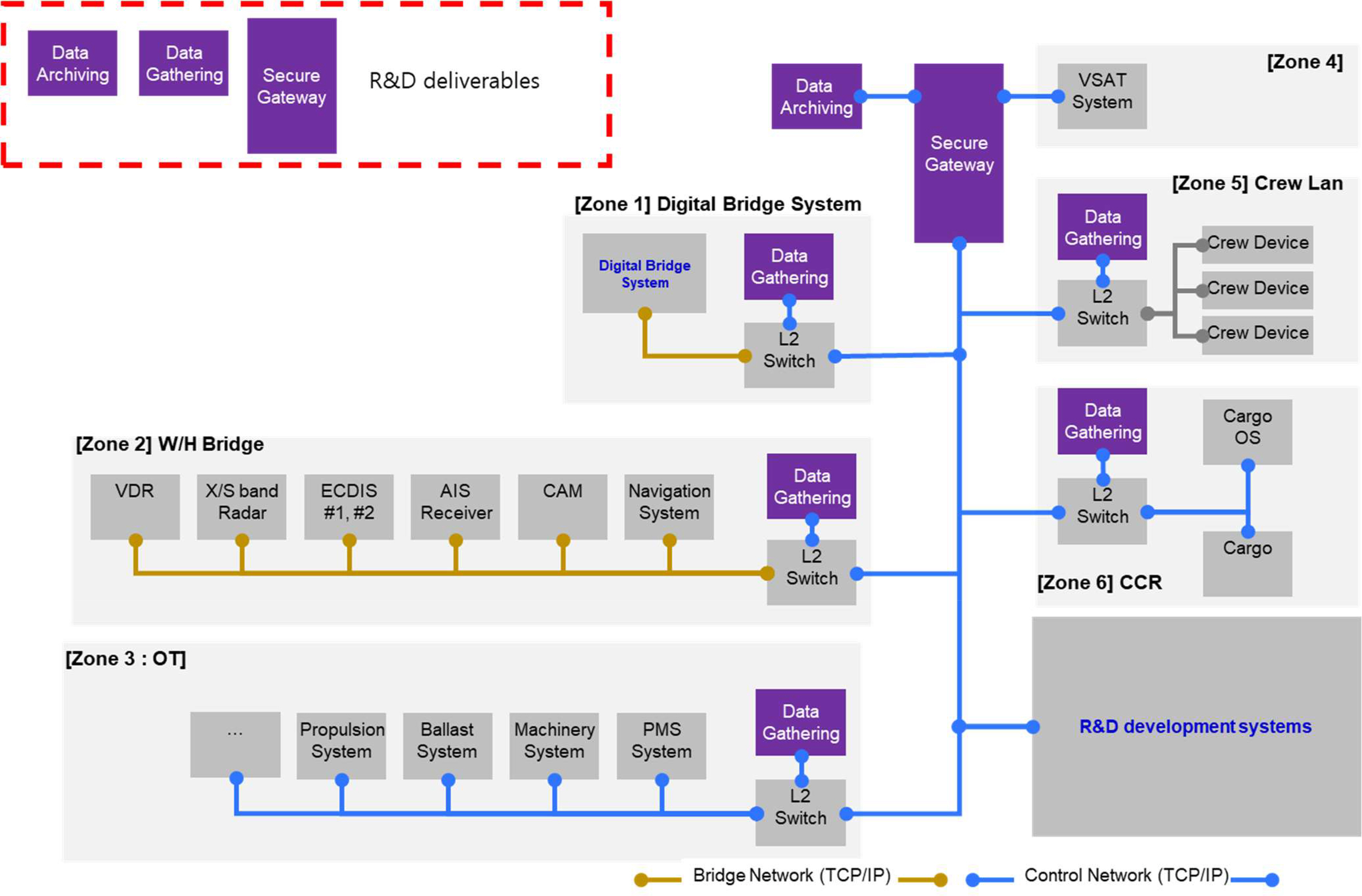
In general, the network of ships to which the concept of cybersecurity is applied is divided into zones, such as bridge systems related to ship operations such as navigation and communication, engine, propulsion systems related to ship propulsion, crew area, cargo management, and handling. As part of the plan to reduce cyber risk in the event of a cyberattack, a cybersecurity composition diagram of autonomous ships, expressed by separating, classifying, and stratifying networks by region, is shown in
Fig. 5.
Considering the current firewalls of commercial equipment, the network topology applicable to MASS ships can be shown in
Fig. 5 by applying Open Systems Interconnection model(OSI) 7 layers(L1: Physical Layer, L2: Data Link Layer, L3: Network Layer, L4: Transport Layer, L5: Session Layer, L6: Presentation Layer, and L7: Application Layer)(ISO/IEC, 1994; Microsoft, 2022). Zone-1 consists of the autonomous operating equipment necessary for the operation of MASS ships, Zone-2 consists of a bridge navigation and communication system, Zone-3 is a propulsion and engine system, Zone-4 is a communication system, Zone-5 is a crew area network system, and Zone-6 consists of a cargo handling system divided into L2 layers. The L2 layer configures the L2 switch and firewall in each zone. In addition, the L3 layer installs the L3 switch for internal or external communication using IP addresses, and the firewall between the L3 switch and satellite communication aims to defend against cyber threats entering ships from the outside(on land).
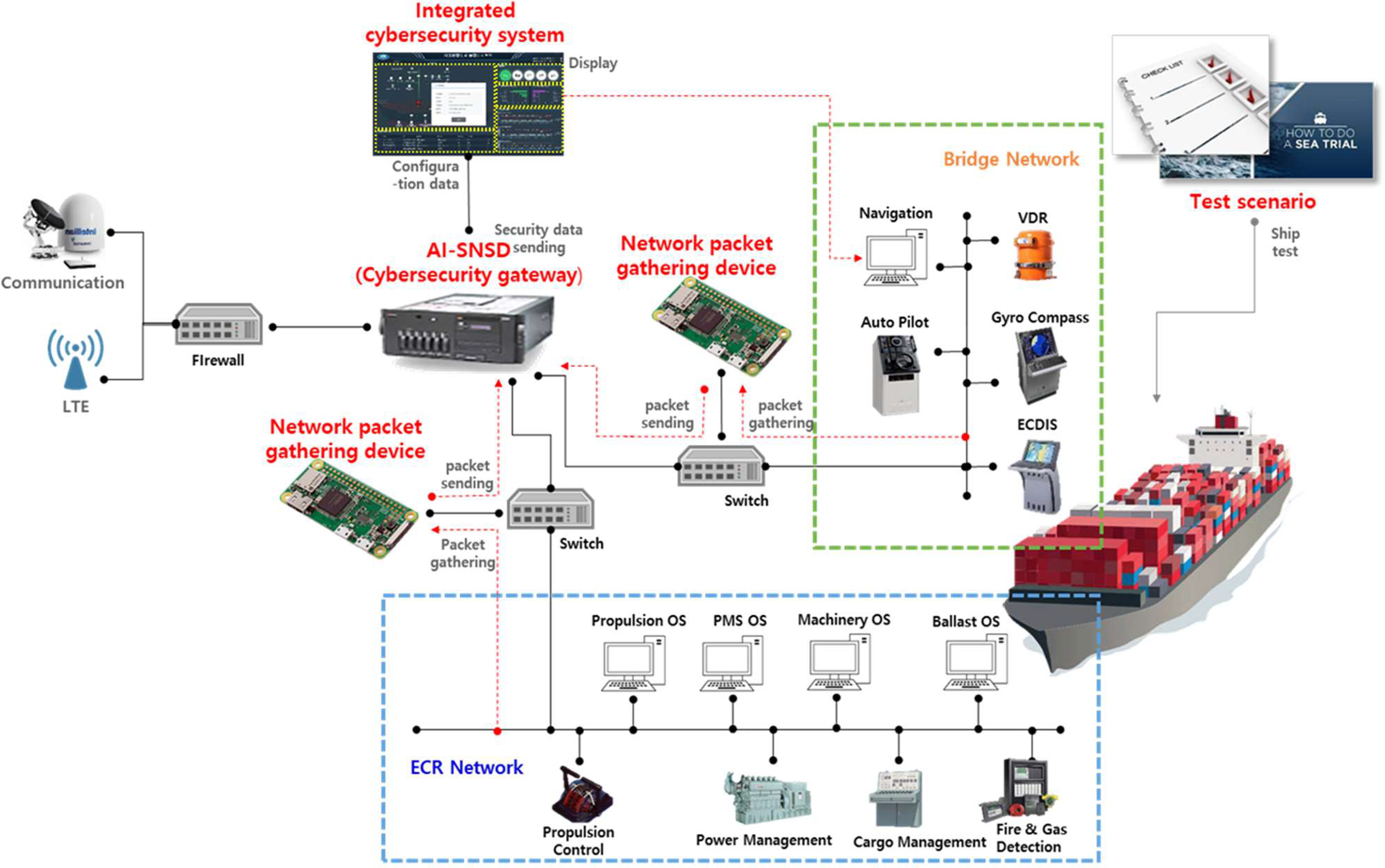
However, when the cybersecurity gateway under development is applied, the network topology of the autonomous ships can be expressed as shown in
Fig. 6. Here, the AI-SNSD, which integrates the functions of the L3 switches and firewalls, was installed without setting the firewall function of the existing L2 layer. Data-gathering equipment is installed to monitor potential cyber risks, and AI-SNSD is deployed to detect and block external attacks. As communication between zones is limited, the system is designed to operate effectively for extended periods without maintenance. Additionally, protocols commonly used on ships are incorporated to enhance the system's ability to respond to cyber threats.
Table 3 compares the main functions of existing firewall equipment and the cybersecurity gateway(AI-SNSD) under development for MASS.
In the case of firewall functions, existing equipment is subject to rule-based and signature-based firewall policies, and AI-ANSD of MASS includes dynamic control over IP and ports in addition to existing firewall functions. In the case of intrusion prevention systems, existing equipment is rule-based and signature-based, whereas AI-SNSD adds a machine-learning-based intrusion prevention function to the intrusion prevention systems(IPS) of existing equipment. In the case of intrusion prevention systems, the existing equipment is the same as in intrusion detection systems(IDS); however, AI-SNSD adds machine-learning-based intrusion prevention functions similar to IPS. For antiviruses and spam detection, the existing equipment requires separate software installation, and for AI-SNSD, DPI-based malware detection is added. There is no significant difference in VPN functions, and existing equipment does not support log/monitoring functions for the entire ship network. However, AI-SNSD collects internal and external network traffic to support log/monitoring functions for the entire ship network. In the case of bringing your own device(BYOD) management, existing equipment requires a separate network access control(NAC) solution, whereas AI-SNSD includes public key infrastructure(PKI) certificate-based BYOD device access management and authentication support. In the case of the network abnormality detection function, the existing equipment supports the detection function for external network traffic, and AI-SNSD also supports the abnormality detection function for internal and external traffic. For the authentication function of external communication, separate PKI infrastructure and software installation are required for existing equipment, and PKI-based ship-to-ship/ship-to-shore/shore-to-shore authentication is supported for AI-SNSD. In the case of the data flow control function, internal communication of the existing equipment is impossible because of the network structure, whereas in the case of AI-SNSD, data flow control is possible without installing a separate product. In addition, existing equipment does not provide routing functions, but AI-SNSD provides routing functions that include security functions suitable for MASS ships.





 PDF Links
PDF Links PubReader
PubReader ePub Link
ePub Link Full text via DOI
Full text via DOI Download Citation
Download Citation Print
Print